V2V and V2I networks are temporary, short-duration wireless networks designed for improving the overall driving experience by exchanging a multitude of information between vehicles and fixed infrastructure. However, given the presence of malicious entities, greedy drivers, and pranksters, blindly accepting any such information received (even one received through a cryptographically secured channel) can be catastrophic. In this project, we focus on building a model for managing (computing and maintaining) the trustworthiness of messages received over V2V networks.
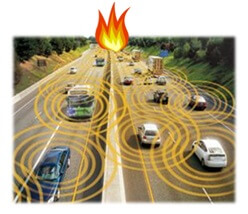
Figure 1: Example Scenario: Traffic Accident Report
Consider a scenario where a vehicle on a highway broadcasts a message with an incident report (e.g., accident, traffic congestion, broken bridge) to the vehicles immediately behind it using the underlying V2V network. Each receiving vehicle forwards the message further downstream. Additionally, if a forwarding vehicle (that is, the user driving it) believes the message itself, it will endorse the message by signing it. A vehicle originating an incident report will always endorse it. Consequently, a vehicle receiving a V2V incident report will have at least one endorsement associated with it. Upon receiving an incident report, a vehicle needs to make a decision on whether it trusts the report based on all the vehicles that have endorsed the report. This decision is taken based on: (1) a trust triple computed for each of the endorsers, and (2) combining the individual endorser trust triples to produce an aggregate trust score for the message.
Several assumptions are made in this regard for effective trust score computation. First, a strong notion of id is assumed for the vehicles. This can be in the form of an e-license or VIN of the vehicle, provided by a centralized registration entity such as state DMV or NHTSA. Second, the vehicle and user (driver) of the vehicle are conceptually considered one entity with the vehicle effectively carrying out the policies of the user. Third, a separate database is assumed that tracks a vehicle’s endorsement history and that can be queried through a V2I link. The user regularly provides updates to this database based on the veracity of the endorser’s information. Fourth, the information obtained over the V2I infrastructure is assumed to be secure from maleficence.
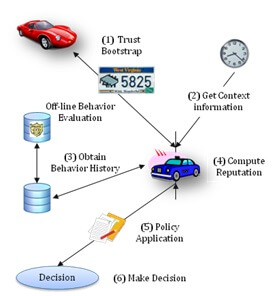
Figure 2: Example Workflow of Proposed Approach
The trust on an endorser is computed as a triple (t, c, f). Here, t is the measured reputation value computed based on the endorser’s history of providing a correct and incorrect endorsement. It could be measured as simply as (# of endorsements of factual reports/total # of endorsements) assuming independence of individual endorsements. The value c is the level of confidence on the measured reputation t, computed based on the goodness of fit of the distribution of the endorser’s behavior to a specific user behavior. Finally, f is the default reputation value that is essential to reason about reports received from a vehicle that does not have any historical information available for it. The value of f is computed using static information about the endorser such as (1) vehicle make (e.g., Ford, BMW, etc.), (2) vehicle model (e.g., Corolla, Focus, etc.), (3) vehicle history (e.g., Carfax report), (4) vehicle type (e.g., ambulance, police car, etc.), (5) context information (e.g., current location: North Philly; current time: 2:00am). The vehicle uses the V2I network to obtain the static information about the endorsers, usually from the registration authority that assigns vehicle ids. Additionally, the user specifies policies to determine f, by explicitly stating its value for various combinations of static and contextual information.
Once the triple (t,c,f) for all the endorsers of the incident report has been computed, they are merged using operators (AND or OR) defined by the message recipient to get an aggregate trust tuple, based on which the final trust score is computed. If T is greater than a threshold (again specified by the context and user), then the report is assumed to be trusted. The user can then join the endorsed user group and forward the message to its neighboring cars.
Other Members:
Cong Liao (Penn Master Student)
Krishna Venkatasubramanian (Assistant Professor at WPI)
Cyber-Physical Systems Week 2012 Poster and Demo Session, Beijing, China, April 2012